Introduction
G'day, g'day, g'day! Today, I’m going for a bit of a wander into passkeys!
What are they?
How do they work?
Should you use them?
Passkeys are a potentially game-changing technology designed to make passwords obsolete. But, as with any new tech—especially one still in its early stages—there are unknowns we need to consider.
We should be asking important questions like:
Are passkeys truly secure?
Could they open us up to novel vulnerabilities?
Whether you’re an individual looking to simplify your logins or representing an organisation considering passkeys, this article is for you. And if you’ve never heard of passkeys before, read on—this is definitely for you.
What are passkeys?
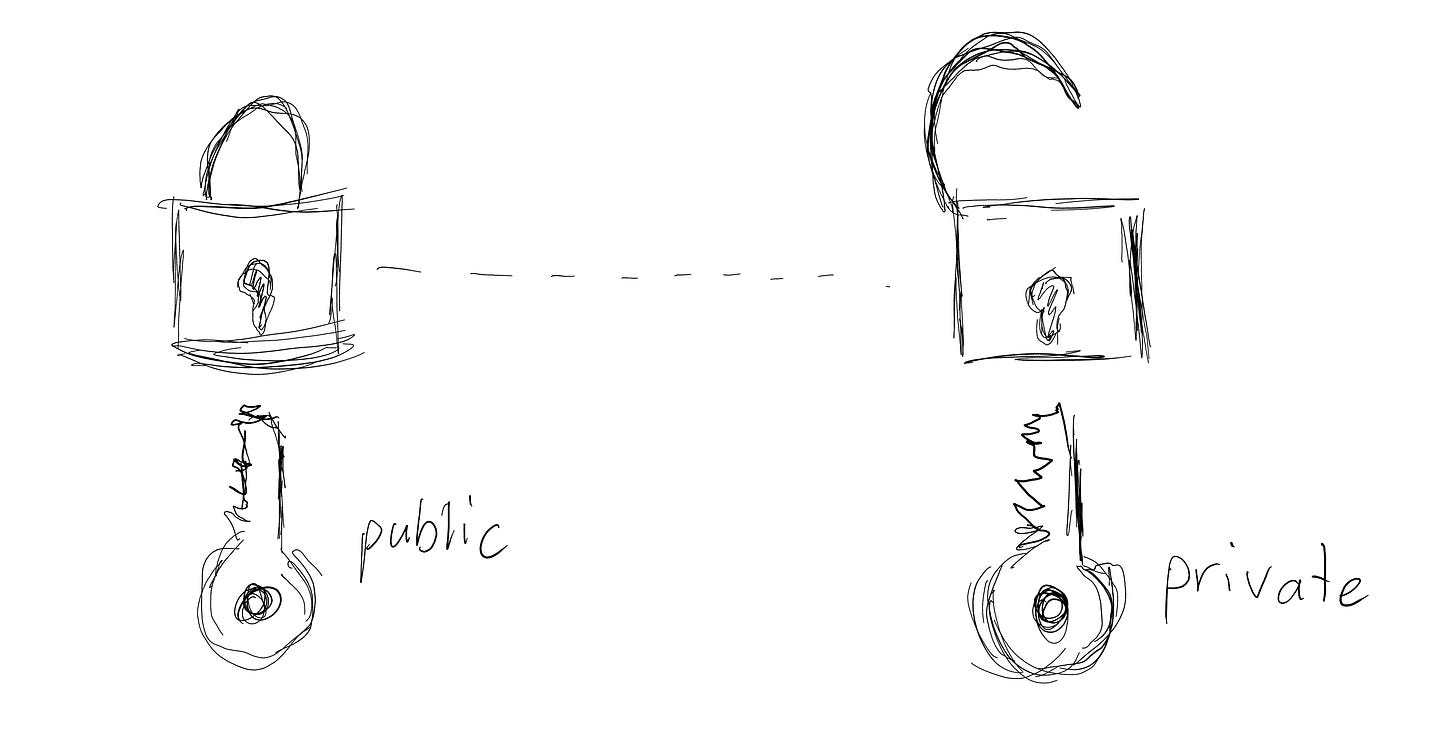
Passkeys are built on public-private key cryptography, the same foundational technology used in many security systems. What’s new is how this technology is being applied to potentially replace traditional passwords altogether.
Big players like Apple, Google, and Microsoft are pushing this innovation, signaling a real effort to change how we authenticate online.
Here’s a simplified explanation:
A private key is securely generated on your device and never leaves it1.
A corresponding public key is sent to the service you’re authenticating with.
When you log in, the service sends a cryptographic challenge. Your device uses the private key to sign the challenge, and the service verifies it using the public key.
Think of it like a lock and key: the private key is your key, securely stored, while the public key is the lock, shared with the service. Together, they ensure only you can "unlock" your account.
What’s so important about passkeys?
Passwords have been a headache for decades—forgotten passwords, phishing attacks, credential stuffing... you name it. Passkeys promise to eliminate these issues.
Could this be the beginning of the end for passwords? Let’s explore.
How do passkeys work?
Passkeys rely on public-private key pairs:
The private key stays on your device and is protected by your biometrics (e.g., fingerprint, face scan) or a PIN.
The public key is stored with the service you’re logging into.
Unlike passwords, private keys never leave your device, making them much harder to steal. They’re also phishing-resistant because they’re tied to the service’s domain and can’t be reused elsewhere.
Why are passkeys so appealing?
Phishing Resistance:
No one can trick you into sharing your passkey because it’s securely stored on your device and inaccessible—even to you.
Convenience:
No more remembering passwords or dealing with annoying resets.
Security:
Passkeys are domain-bound, meaning they’re tied to the specific service where they were created. This mitigates credential stuffing and brute-force attacks.
Savings, savings, savings (for organisations):
Password resets are one of the top reasons users contact IT support. Passkeys could reduce these burdens significantly.
Challenges and unknowns
Nothing is perfect, and passkeys are no exception. While they are promising, there are challenges and unknowns we should address:
Device dependency:
What happens if you lose your phone or laptop? How robust are the recovery mechanisms?
Cloud syncing risks:
Many passkey systems rely on syncing private keys through cloud services. While convenient, this introduces a potential attack vector.
Adoption barriers:
Not all websites and services support passkeys yet, and partial rollouts could frustrate users.
Unknown vulnerabilities:
Passkeys are still new. Could supply chain attacks target the hardware storing private keys, like Trusted Platform Modules (TPMs)?
Could the WebAuthn API or browser implementations become attack vectors?
These are open questions, and as with any emerging technology, it’s not a matter of if vulnerabilities will appear—it’s a matter of when.
Should you adopt your very own passkeys?
Are passkeys right for YOU?
For individuals:
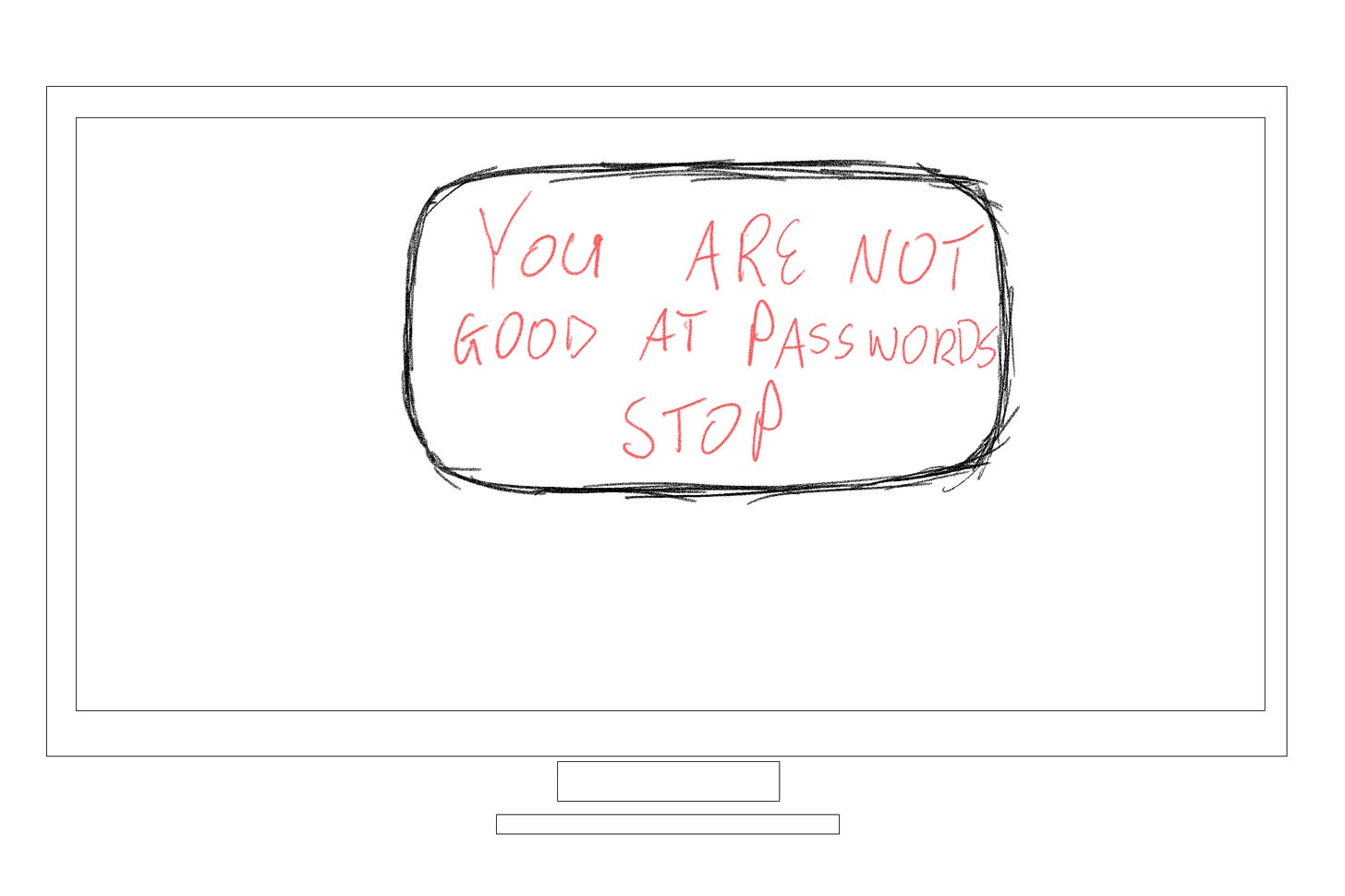
If you value security and convenience, passkeys might be worth exploring. However, as with any new technology, there will likely be some hiccups along the way.Alternatively, if you’ve ever seen the message below, you should considering using passkeys:
For organisations:
Consider your specific use case:Do you manage high-value accounts that need extra security?
Are your users tech-savvy enough to adapt to this change?
How well will passkeys integrate with your existing systems?
If your organisation relies on legacy systems or serves less tech-savvy users, it might make sense to wait until the technology matures.
What’s next for passkeys?
Here are some big questions for the future:
Will Apple, Google, and Microsoft collaborate to make passkeys universally adopted, or will they remain siloed within their ecosystems?
Could attackers find ways to trick users into generating passkeys for malicious websites?
What happens if a major cloud service used for syncing passkeys is compromised?
While passkeys represent a shift toward a balance between security and convenience, there is no silver bullet. Maintaining vigilance and healthy skepticism is essential.
Final passthrough for passkeys
Thanks for reading (or listening, if this becomes an audio episode). Whether you’re on the fence about passkeys or already considering them, I hope this gave you something to think about.
Here are some follow-up questions:
Would you trust passkeys for your most critical accounts?
Have you tried setting them up on your device?
Drop a comment and share your thoughts—I’d love to hear from you.
Until next time,
stay safe,
stay curious, and
keep thinking critically.
See ya!
\
This isn’t strictly true—I’m working on another article that goes into a bit more detail and clears up some of the marketing fluff.





Nice! 100% agree on the length > complexity! So does maths haha. I put together a program that displays it, actually. Maybe I'll publish it.
Also been researching passkeys a bit and I can see some potential vulnerabilities and risk shifting. I'll write about it if course. I find it all pretty interesting and it's fun to think about all the novel ways people might exploit new and upcoming tech innovations!
I've adopted it for websites or account i'm not too worried about. My password game is way stronger. Length >>> combination and it's been convenient for me.
I trust Apple a bit more than the rest but today, i got a scam mail impersonating apple so there's that.