The Substack Phishing Expedition, ahem, Epidemic, uhh I Mean Minor Problem?
Check Out The Latest in Title Word Salad
Hi everyone!
Just noticed this post by Substack Writers (add the link to the note here ya silly bugger, or forget it and readers will get a humorous Easter egg),
and I wanted to add some extra advice about phishing in general as well as on Substack.
I haven’t been active enough long enough on Substack to understand the prevalence of phishing and other attacks on Substack. However, if it’s being posted about (seen a couple now) then it’s worth addressing!
What is Phishing?
There’s plenty of resources online that go on endlessly about phishing, but you want to come here for the best, no nonsense, actionable advice and information with a casual tone and maybe even some humour mixed in (dry or otherwise). My day job involves some of this1
and some of this2
you can trust me, this is the Internet and everyone tells the truth, no but seriously I’m telling the truth—okay shut up before you lose them!
You know what this thing is?3
That’s right, fishing rod—I can tell you’re already an expert, I still have to press on because I told myself I would write this article.
Now imagine that instead of bait they had some enticing information—imagine like a special offer, a one-of-a-kind invite to something. For Substack I imagine this would look something like an invitation to a special writing nook online. And instead of a fishing rod, they had a phishing rod, uhh, I mean a keyboard, or perhaps a well-crafted email (or in this case, a Substack DM!) designed to snag your attention. In email form, the subject would likely be something that seems too tempting to ignore. The usual are things like, you’ve won an award, an urgent message from what looks like your bank (wait I don’t remember having an account with that bank…). Here’s the kicker, it’s all an elaborate ruse! Trickery, absolutely tomfoolery of the highest order!
Your confidence might tell you, “I’d never fall for something so obvious!” Let’s get our cockney cockiness in-check. There’s a craftiness afoot, and these Internet-anglers are the craftiest of the crafty. They can make things look pretty legit, and it’s not just regular folks that get hooked, there have been prominent YouTubers (in the cybersecurity space) that have fallen victim to some (granted more sophisticated, targeted) phishing attacks. I couldn’t remember who it was, but one YouTuber had their account taken over, videos deleted—they were able to recover and lessons were learned!
How Did They Know / Find Out X About Me?
If you’re referring to, for example, your email address—most likely from a data breach, millions of email addresses get leaked online. If you’re asking how they knew to target you on Substack through DMs, most likely they didn’t know they were just using a shotgun approach. Which is a lot easier on a place like Substack, because what do we all want to be? Famous god-damn writers, that’s right! They already know our weakness! Other than that, the amount of information you put online about yourself is exponentially proportional to the risk of being being successfully phished.
please note I totally made this up, here’s a silly image to legitimise my joke:4
Legitimately, this is how the crafty buggers are able to craft (if they are the type to craft, and are not too daft ← see what I did there) seemingly personalised emails / messages to people in hopes they will click on their golden link of destiny, because they’ve done their research. They’ve scoured the Internet for information about you, stalked your Facebook, your LinkedIn, your entire digital footprint—what I’m describing here is actually referred to as spear phishing, and if you’re a target of spear phishing you’re a lot more important than me or others likely to be reading this awesome post!
How Can I Lop Their Heads Off Protect Myself?
Be careful what you click! A link can be made to look like anything (not anything, don’t be silly, I’m being hyperbolic). For example, I’m going to try and create a ‘tricky’ link right in this post, if it doesn’t work, I’ll go to plan B:
https://totallylegitwebsite.com
Oh would you look at that! You thought you were going to https://totallylegitwebsite.com but I fooled you and I have actually sent you to my latest second-latest post Much Ado About Substack (https://open.substack.com/pub/thirteenthstrike/p/much-ado-about-substack?r=319z6g&utm_campaign=post&utm_medium=web&showWelcomeOnShare=true). If you hover your mouse (for those reading from their desktop), your browser will show you the real link. Another example:5
Zoomed in:6
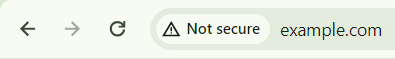
Another thing to be on the lookout for in the link, is whether it’s ‘secure’.
Most browsers in this day and age won’t let you visit HTTP (no ‘s’) websites, they will actually ‘upgrade’ you to the secure version. If you happen to visit a website that doesn’t support an HTTPS version, you’ll see something similar to this:7
A big warning telling you the website is not secure.
There are, however, legitimate reasons or circumstances where it’s okay (or necessary) to visit or use HTTP websites, such as:
Accessing old or archived content—some niche or random blog that hasn’t been updated since 1999 isn’t likely to be rocking the latest in HTTPS technology
Local network applications—maybe one day you had this genius idea to learn about web development technology and spun up
nginxlocally on your computer so you can create your totally awesome Personal Motivation Dashboard, yeah this will be served through ol’ port 80 (HTTP)Public information sites—there may still be some of these floating around that simply serve public information and don’t require you to log in or submit any personal information
Other external factors—in some regions or particular scenarios (restrictive network environments, etc.) HTTPS may not be feasible or it could be intentionally blocked, whereby the only option is to use HTTP—just be careful you don’t submit personal information, passwords, and so on!
What Can I Do if I Fumble My Way to One of These Fiendish Future Felons?
They will most likely do this under the cover of DMs, so your best option is to click the little three dots to the right of the chat bubble / thread:8
Once you click then you’re well on your way! Oh and then click the report button:9
The big red one, you can’t miss it—well I guess you could if you really tried.
Note: You can report a thread but for these scammers / phishers it would be better to head to their profile directly and report them from there—the process is more or less the same but from their profile instead of the chat thread.
Then, you come to this screen:
My advice here would be to be as descriptive as possible, be clear and give any other relevant information that you can (even if it’s from outside Substack) to help as much as you can. Ignore the Optional, in my opinion, we all gotta help each other out, ya know?
Further / General Advice
I’ll keep this short and sweet (maybe a little sour for some).
Enable 2FA (two-factor authentication) and your recovery questions for Substack, and any other websites / services you use online
Where do I find this option? HERE:
Click the above button—not literally that one, the one one your profile, it’ll hopefully have a different image (yours 😉) then go to Settings (yes you can click this link, it’s like magic—though definitely open it in a new tab, you can do that by clicking with your middle mouse button on desktop). Scroll all the way to the bottom of the page to
Account Securityand run through the process of turning them both on.TIP: It’s preferable if you don’t use real information for your recovery question answers—a simple example might be:
What was your first pet’s name?
Instead of putting
Scruffsor whatever your pet’s name was, use your password manager (yes, you definitely have one and if you don’t you should run out and grab one) to generate something like:animation decode conducive pacifist swear decreaseWith that number of characters and spaces, you would be looking at a pool of around
7,45e+45 (7,450,000,000,000,000,000,000,000,000,000,000,000,000)possible combinations—looking purely at the characters, not taking into account useable English words, etc.—okay getting too complicated!Compare that with someone who stalked your profile and saw that tagged pic you have of
Scruffsfrom 2009—which do you think would be the most guessable?
Create strong passwords (see my earlier point about password managers)
At least 8 characters; and avoid10
Passwords obtained from previous breach corpuses—translation, if it’s been leaked online you shouldn’t use it, examples of the top 10 worst passwords:
"123456"
"password"
"123456789"
"12345"
"12345678"
"qwerty"
"111111"
"123123"
"1234567890"
"1234567"
Dictionary words—this is referring to single, easy-to-guess words, like, oh I don’t know,
“password”Repetitive or sequential characters (e.g. ‘aaaaaa’, ‘1234abcd’).
Context-specific words, such as the name of the service, the username, and derivatives thereof.
Conclu-shun the Phishers
And that’s about it for this post—your not-so-average guide to staying afloat in the phishing-infested waters of the digital world, Substack and beyond. Doesn’t matter if you’re a Substack superstar or getting your walking appendages wet, being savvy about the sneaky world of phishing is crucial. It’s not simply about dodgy the odd fishing email; it’s about safeguarding your digital presence against those crafty cyber-anglers.
Remember, confidence confidence is king, but overconfidence is phishing bait! It doesn’t matter how tech-savvy you are, there’s always a craftier phisher out there, ready to reel you in with more than nautical-themed puns. The tales of fallen YouTubers and lists of hauntingly bad passwords should be stark reminders that we’re all potentially one click away from digital disaster.
But hey, equipping ourselves with knowledge, wielding the hammer of skepticism and arming our accounts with layers of security (g’day, two-factor authentication) can make us all formidable foes against those felonious phishing fiends.
So, got a story from the digital depths? Ever snagged yourself a phishing line? Feel free to share any stories, tips or even your fishiest phishy jokes in the comments. Let’s create our own whirlpool of wisdom without withering away into the phisher’s whirlpool—share the knowledge and we can stay informed and ahead of those cyber scallywags.
That's it for now as always, good luck, stay safe and be well.
Image source: Me, I drew it
Image source: Me, I drew it
Image source: Me, I drew it
Image source: Me, I drew it
Image source: Screenshot boiiii
Image source: Screenshot boiiii
Image source: Screenshot boiiii













This entire post is such a mood but the footnotes really brought it home for me