How Password Managers Protect Your Passwords
The Magic Behind Password Management and Why It Matters
Why Does It Matter?
Did you know in 2020, 80% of breaches involved stolen creds (that's short for credentials)—a lot due to poor password management.
In this article I'm gonna go through how password managers "work" and how they can give you better digital security.
In 2023, wannabe eugenics company 23andMe suffered a large data breach affecting 14 million of its users. The cause? Yep, stolen credentials—hackers were offering to sell the data. The funniest part about the breach was something I found in one of their statements regarding the breach, specifically this part:
We believe that the threat actor may have then, in violation of our Terms of Service, accessed 23andMe.com accounts without authorization and obtained information from certain accounts, including information about users’ DNA Relatives profiles, to the extent a user opted into that service.1
Why is it funny? Here’s a lesson on technicalities. Authorisation means something specific in cybersecurity. It means that someone is allowed to access a system. Authentication, on the other hand is the process of proving your "identity," which in this case is the correct username and password.
The hilarious part is that by providing the right credentials (albeit stolen), the hackers were authorised to log in. They successfully authenticated to 23andMe—they presented the right information. A CAPTCHA requires more "authentication" of humanness, than a simple username/password login—the computer/website doesn't know the difference. You got the details, you get the access.
Yes, the hackers violated the trust of the users they stole from, and they may have violated 23andMe's Terms of Service—I didn't dig that deep, if you know shout it out in the comments!
Have you ever left your house key under the mat at the front door? Used one of those fake rocks? It's the same as you getting angry at someone discovering this and then "breaking in"...using your own key. How dare you find my hiding place and then use my actual key to let yourself in!
Bottom line is their users would have benefited greatly from the use of password managers.
What do you think about 23andMe’s response?
Why should you care about password managers?
For one, the story above could have been you. You could have been (or perhaps were) one of the people affected by this data breach. The tools and practices of organisations should protect your digital privacy, that doesn't mean you shouldn't take measures to mitigate potential breaches. This includes password protection.
Password managers aren’t just a convenience tool—they’ve objectively been making your (and your company’s) credentials and the internet overall a safer place.
Key Terms—Cementing the Foundation
Below are some terms you can chew on for a bit before I get into the weeds of the article.
Password Manager
Think of password managers simply as a secure vault, a virtual safe to store information. That's right, password managers aren't just limited to storing passwords. See below for a screenshot of Bitwarden.
Categories of information you can store in Bitwarden

Hashing
Hashing is a one-way cryptographic function that is super difficult, if not practically impossible to reverse. Whoa, slow down there, egghead—crypto-what-a-hootinany? I'll use an analogy so it's not easier to digest. You gotta be a bit of a brainiac to fully understand cryptography at a deep level (don't look at me like that, I don't fall under that category).
What about a paper shredder? Not just a regular paper shredder but a cross-cut one—the type that really does a number on all paper that enters its snout.
Remember—often times I'll use analogies that could easily be "torn to sheds" (hah) by people who want to misunderstand to try and show how smart they (think) they are. The point of my analogies is to give you lovely readers the very general ideas about difficult-to-understand concepts.
The point is, hashing is a process for making plaintext ("password 1234") and turn it into something that's not readable in the same way, something scrambled ("b1a87f320dbdedcfbcdc35976518a42e60530dd4656398c86945e4954ab71e32") mmm eggs.
Doing this makes it harder to attackers to use credentials they’ve stolen.
A hash is symmetric cryptography.
Salts
After a while of using hashes, we discovered there were patterns to the outputs and some algorithms had weaknesses. This isn't ideal if you're trying to keep people from understanding the information you have stored—things like your dog's pooping habits, for example.
Sprinkle some salt!
A salt is some random data added after the hash string. If we apply a salt to our hashed string from earlier, we get "db5b3ea4810f5a35eb98fc1fd5d9d5cb0729611942f08c3ec4d6218ef5589fee". Looks a lot different! The idea behind salts is that it makes hashed outputs unpredictable by adding random elements. They are unique, just like you (d’awww).
Encryption
First off—encryption and hashing aren't the same thing!
When you generate a hash, there's no way back—they're not reversible. Encryption on the other hand is designed to be "reversed", but only by the right person.
The easiest way to understand encryption is the good ol' padlock and key. Or safe and combination.
A padlock and key is literally the examples that litter everywhere, even within security circles—let’s go with the tried and true.
When you lock the padlock, this is encrypting.
When you unlock the padlock, this is decrypting.
Imagine a Schroedinger's safe. When it’s open (unlocked, decrypted) you can see everything that’s in it. When it’s closed (locked, encrypted) you don’t know whether there’s anything in it or not—all you know is it’s locked. You’d need the combination to open it.
Encryption is asymmetric cryptography.
It’s about scrambling your vault data into a secret code that can only be deciphered by someone with the decryption key. The goal is to make stolen data as useless as possible (one of, anyway).
The Risks: Why You Need a Password Manager
Stolen Credentials
The number one reason you should be using a password manager is because hackers exploit reused passwords to breach multiple accounts. Where do they get these passwords? From database breaches. Some companies don't store user credentials securely. When they get hacked or breached, all user emails and passwords can be easily extracted and sold on the black market or used to extort the company for ransom money. Sometimes these companies will pay a ransom up to 3 or 4 times for the same breach!

Data used in the above graph is from the ‘2024 Data Breach Investigations Report’ (DBIR) - Verizon2
Another reason to use a password manager will hit closer to home. I wanna ask you:
What's your password hygiene like at the moment?
Are you writing passwords and login details on sticky notes (physical or digital)?
Reusing the same password across multiple accounts?
Is your "go-to" password something anyone who knows you could guess?
Let me rephrase that question to put things in perspective for you:
How much would it impact your life if someone logged into your main email account, changed the login details, then started emptying your bank accounts? Imagine they also began impersonating you—taking out massive loans in your name all across the country.
How long would it take to get your life back on track?
Lastly, what if you simply forget your login details to critical accounts?
All of the above reasons are enough to justify you at least considering a password manager. Wouldn't you agree?
Human Error
Human error still ranks highly as a contributor in breaches. From 2020 to 2024 the numbers haven’t declined anywhere near as dramatically as stolen credentials being used in breaches.
Password managers are one explanation for the drop in the “human-in-the-loop” problem. Other explanations include
Multi-factor authentication (MFA) adoption
Secrets automation
OAuth-based authentication
API improvements
Zero trust
Security Awareness and training
Attackers shifting to other vectors
Regulatory enforcement and industry standards adoption
I’d love to have subscriber discussion threads about privacy and security:
Practical Risks Without Password Managers
Forgetting login details
Weak passwords
Password / credential reuse
How Password Managers Secure Your Passwords
Creating Your Master Password
When you create your master password, it’s hashed and salted—this ensures it is never stored or known by the password manager. Instead, the hashed, salted value is used to verify and unlock your vault.
Your Vault, Encrypted
Data generally exists in two states:
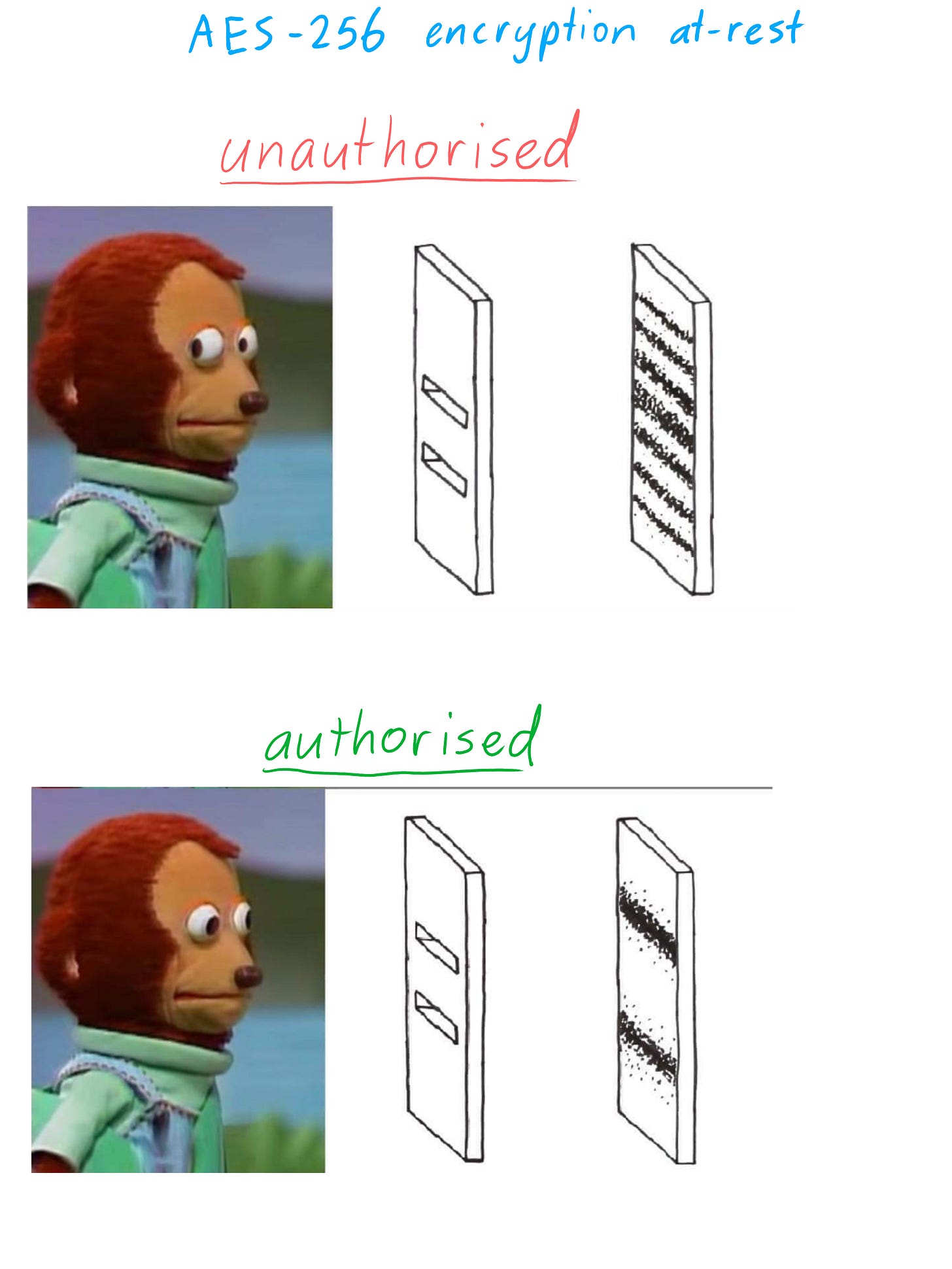
At-rest
Your data (password vault in this case) is sitting around doing not much (vault is idle) it is protected by AES-256 encryption.
Side-note
I remember first thinking about this concept many years ago and being utterly confused. I understood what encryption was (sort of, it’s one of those things where the more you learn, the less you realise you understand), but when I thought about how something could be encrypted, while at the same time I could be looking at information that looked suspiciously unencrypted, had me baffled.
Have a look at the image below for the simplest explanation I could muster:
In-transit
When passwords are on the move (e.g., transmitted, syncing to your devices), they are encrypted in-transit using secure tunnels (“wrapped” in encryption).
Plain-text data is never exposed—your data is decrypted locally on your computer or phone.
Stronk Password Generation
If you wanted to randomly generate a password manually (like a password manager does), you'd need to roll a 100-sided die for each character (letter, number, symbol, etc.). For a 20-character password across 50 websites, that’s 1,000 die rolls—nah, I’ll be right, thanks!
Password managers use cryptographically secure pseudorandom number generators.
For example:
Bitwarden leverages secure randomness from the operating system.
C# Implementation: RNGCryptoServiceProvider class (standard .NET crypto)
Web Environments: window.crypto.getRandomValues() via the Web Crypto API
Password Detection and Autofill
How do password managers securely autofill passwords? Take Bitwarden’s browser extension as an example:
Uses content scripts to detect login fields on a web page via the Document Object Model (DOM).
Performs these functions securely because the extension is:
Sandboxed (isolated from the web page content)
Injecting autofill interfaces using shadow DOM elements with randomized names
Using background scripts to facilitate secure communication
Risks of Using a Password Manager
There are trade-offs and risks with everything, and password managers are no exception. I mentioned earlier about companies getting breached by hackers—password managers, especially cloud-based ones, are no different. They store data much like any other company. However, password managers store all the details you use to log into websites (and other sensitive data).
Unlike most companies, cloud-based password managers rely heavily on user trust—it’s the core of their business model. This means they have a much bigger obligation to securely store your data and ensure it can't be accessed by anyone except you. They create a secure password vault for you.
How LastPass Messed Up
On August 25, 2022, LastPass disclosed they had been breached3. Customer data was stolen, but they reassured users their data was safely encrypted using the master password. They emphasized that users' master passwords are never known by the company.
Unfortunately, the situation turned out to be much worse than initially reported. Attackers began breaking into user vaults that had weak master passwords.
Personally, I moved away from LastPass long before this occurred—around the time they were acquired by LogMeIn in 20154. Bitwarden, from what I know, is yet to have any major breaches.
Other Risks
Over-reliance
Becoming too reliant on a password manager can be risky. You must remember and keep your master password safe.
Personal biases
Many people fall into a false sense of security and overlook best practices until they experience the worst-case scenario.
That said, the risks of not using a password manager far outweigh the risks of using one.
What Makes a Good Password?
Length. The end.
Okay, maybe not just length, but if forced to choose, length beats complexity every time—even on Sundays!
This could be a whole other article so I won’t get into all the details here.
Benefits of Password Managers
Improved password strength
Avoiding password reuse
Secure password storage
These practices reduce the risk of account takeovers, identity theft, and financial loss, while also giving you peace of mind.
Using a password manager is the easiest way to protect yourself from the real risks outlined above.
Conclusion
I outlined above the risks of using password managers, but more importantly, the risks of not using them. You can see from real-world examples the impact poor password hygiene and cybersecurity practices have on businesses and individuals. The data-backed information shows how password managers and better security habits greatly improve security for everyone.
Remember, the risks of not using a password manager outweigh the trade-offs of using them.
That’s all for now.
As always,
Good luck,
Stay safe and,
Be well.
See ya!
P.S.
If there are any terms, theories or anything you don’t understand from my article, don’t hesitate to reach out, leave a comment, tag me in a note with your question.
I want to make my writing and content accessible—find the bravery to ask dumb questions (I ask them all the time)!
https://blog.23andme.com/articles/addressing-data-security-concerns
https://www.verizon.com/business/resources/T26c/reports/2024-dbir-data-breach-investigations-report.pdf
https://blog.lastpass.com/posts/notice-of-recent-security-incident
https://www.zdnet.com/article/lastpass-bought-by-logmein-for-110-million/